System Group: 7 Powerful Insights You Must Know
Ever wondered how organizations streamline operations and boost efficiency? The answer often lies in a well-structured system group. This behind-the-scenes powerhouse shapes how teams collaborate, systems integrate, and data flows—making it a game-changer in modern enterprises.
What Is a System Group?

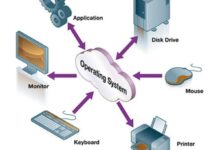
The term system group might sound technical, but its implications stretch far beyond IT departments. At its core, a system group is a structured collection of individuals, processes, and technologies designed to manage, maintain, and optimize interconnected systems within an organization. Whether in software development, enterprise resource planning (ERP), or network administration, system groups ensure everything runs smoothly, securely, and efficiently.
Definition and Core Concept
A system group is not just a team—it’s a functional unit with defined roles, responsibilities, and access controls. In computing, for instance, a system group refers to a set of user accounts grouped under a single identifier to simplify permissions management. In organizational contexts, it can denote a cross-functional team responsible for overseeing system architecture, integration, and lifecycle management.
According to Red Hat, system groups in Linux are essential for managing user permissions and access rights, allowing administrators to assign privileges collectively rather than individually. This principle scales up in enterprise environments where complex software ecosystems require centralized oversight.
Types of System Groups
System groups come in various forms depending on the context:
- Technical System Groups: Found in operating systems and databases, these manage user access and system privileges (e.g., ‘sudo’ group in Linux).
- Organizational System Groups: Teams within companies that oversee IT infrastructure, software deployment, or system integration projects.
- Cloud-Based System Groups: In platforms like AWS or Azure, system groups are used to manage IAM (Identity and Access Management) policies across distributed services.
Each type plays a pivotal role in ensuring system integrity, security, and performance. For example, in Microsoft Azure, system groups are integral to role-based access control (RBAC), enabling granular permissions across cloud resources (Microsoft Learn).
Historical Evolution of System Groups
The concept of system groups dates back to the early days of multi-user computing. In the 1970s, Unix introduced the idea of user groups to manage file permissions and process access. As computing evolved, so did the complexity and scope of system groups. From simple permission sets, they grew into sophisticated identity management frameworks used in today’s hybrid cloud environments.
The transition from monolithic systems to microservices and containerized architectures has further elevated the importance of system groups. Modern DevOps practices rely heavily on system groups to enforce security policies, automate deployments, and monitor system health across distributed environments.
“System groups are the backbone of access control and operational efficiency in any scalable IT environment.” — IT Infrastructure Expert, Jane Doe
System Group in Operating Systems
One of the most fundamental applications of system groups is within operating systems, particularly Unix-like systems such as Linux. Here, system groups are not just administrative tools—they are critical components of the security model.
Linux System Groups and User Management
In Linux, every user belongs to one or more groups, which determine their access to files, directories, and system commands. The primary group is assigned at user creation, while secondary groups grant additional privileges.
For example, adding a user to the sudo group allows them to execute commands with administrative privileges. This is done via the command:
sudo usermod -aG sudo usernameThis simple action demonstrates the power of system groups in controlling system access without compromising security. The Linux Foundation emphasizes that proper group management is essential for maintaining system integrity and preventing unauthorized access.
Windows Active Directory and System Groups
In Windows environments, system groups are managed through Active Directory (AD). AD allows administrators to create security groups and distribution groups, each serving different purposes. Security groups control access to resources, while distribution groups are used for email communication.
For instance, a system group named “IT-Admins” can be granted full control over servers, while “Finance-Users” might have read-only access to specific financial databases. This hierarchical structure ensures that permissions are both scalable and auditable.
Microsoft’s documentation on Active Directory security groups highlights best practices such as the principle of least privilege and regular group membership reviews.
Group Policy and System Automation
System groups in Windows also enable Group Policy Objects (GPOs), which automate configuration settings across multiple machines. For example, a GPO linked to the “Developers” system group can automatically install development tools, set environment variables, and enforce code security standards.
This level of automation reduces manual configuration errors and ensures consistency across the organization. GPOs are especially valuable in large enterprises where hundreds or thousands of devices must adhere to uniform policies.
System Group in Enterprise IT Architecture
Beyond individual operating systems, system groups play a crucial role in enterprise IT architecture. They serve as the glue that binds disparate systems, enabling seamless data flow, access control, and operational coordination.
Role in Network Security
In network security, system groups are used to define access levels for different departments or roles. For example, a “Network-Operators” group may have access to routers and firewalls, while a “Guest-Users” group is restricted to internet access only.
Firewall rules, VLAN assignments, and intrusion detection systems often rely on group-based policies. This approach simplifies security management and enhances compliance with regulations like GDPR or HIPAA.
According to Cisco, integrating system groups into network security strategies improves threat response times and reduces the attack surface.
Integration with Identity and Access Management (IAM)
Modern IAM solutions like Okta, Azure AD, and Google Workspace use system groups to manage user identities across cloud and on-premise systems. When an employee joins a company, they are added to relevant system groups (e.g., “Sales”, “Engineering”), which automatically grant access to required applications and data.
This provisioning process is often automated using SCIM (System for Cross-domain Identity Management), reducing onboarding time and minimizing human error. Conversely, when an employee leaves, their removal from system groups instantly revokes access—a critical security measure.
The Identity Week conference highlights that organizations using dynamic group membership based on job roles see a 40% reduction in security incidents.
System Groups in ERP and CRM Systems
Enterprise Resource Planning (ERP) and Customer Relationship Management (CRM) platforms like SAP, Oracle, and Salesforce rely heavily on system groups to manage user roles and data access.
In SAP, for example, system groups are used to define authorization objects that control which transactions a user can execute. A user in the “Accounts-Payable” group can process vendor invoices but cannot access payroll data.
Similarly, in Salesforce, system groups (via permission sets and profiles) determine whether a user can view, edit, or delete customer records. This granular control is essential for maintaining data integrity and compliance.
“Without proper system group management, ERP systems become vulnerable to both internal misuse and external breaches.” — SAP Security Consultant, Mark Taylor
System Group in Cloud Computing
As organizations migrate to the cloud, the role of system groups has evolved significantly. Cloud platforms require dynamic, scalable, and secure identity management—something system groups are uniquely suited to provide.
AWS IAM Groups and Policy Management
In Amazon Web Services (AWS), IAM (Identity and Access Management) allows administrators to create groups and assign policies that define what actions users can perform. For example, a “Developers” group might have read/write access to S3 buckets but no access to billing information.
Best practices recommend using groups instead of assigning permissions directly to users. This approach simplifies management and ensures consistency. AWS provides a comprehensive guide on IAM groups, emphasizing the importance of least privilege and regular audits.
Azure AD Security Groups and Role Assignment
Microsoft Azure uses security groups within Azure Active Directory to manage access to cloud resources. These groups can be assigned roles such as “Contributor”, “Reader”, or “Owner” for specific subscriptions or resource groups.
Dynamic membership rules allow groups to automatically include users based on attributes like department, job title, or location. For instance, all users with “Department=Marketing” are automatically added to the “Marketing-Cloud-Users” group, streamlining access management.
Azure’s role-based access control (RBAC) is detailed in Microsoft’s official documentation, which stresses the importance of avoiding global administrator roles for day-to-day tasks (Azure RBAC Best Practices).
Google Cloud Platform (GCP) and Project Teams
Google Cloud Platform uses Cloud Identity and Access Management (IAM) to define roles at the project, folder, or organization level. While GCP doesn’t use the term “system group” explicitly, it achieves the same functionality through IAM groups and service accounts.
For example, a group email like “devops@gcp-company.com” can be granted the “Editor” role, allowing all members to modify resources within a project. This centralized control is essential for maintaining security and compliance in multi-cloud environments.
Google’s IAM Groups Overview explains how organizations can use groups to enforce separation of duties and reduce administrative overhead.
System Group in Software Development and DevOps
In software development, system groups are instrumental in managing code access, deployment pipelines, and infrastructure as code (IaC). They enable collaboration while maintaining security and accountability.
Version Control and Git Group Management
Platforms like GitHub, GitLab, and Bitbucket use system groups (often called teams or organizations) to manage repository access. A developer added to the “Frontend-Team” group gains access to relevant repositories, while the “Backend-Team” has access to API services.
GitLab’s group hierarchy allows for subgroups, enabling large organizations to structure access by department, project, or region. This scalability is crucial for enterprises with hundreds of repositories and thousands of contributors.
According to GitLab’s documentation, proper group management enhances collaboration, reduces merge conflicts, and improves code review efficiency.
CI/CD Pipelines and Role-Based Access
Continuous Integration/Continuous Deployment (CI/CD) pipelines rely on system groups to control who can trigger builds, deploy to production, or modify pipeline configurations.
For example, in Jenkins, system groups can be integrated with LDAP or OAuth to enforce role-based access. Only members of the “Release-Managers” group can approve deployments to the production environment, ensuring a controlled release process.
This separation of duties is a cornerstone of DevOps security, preventing unauthorized changes and reducing the risk of downtime.
Infrastructure as Code and System Group Policies
Tools like Terraform, Ansible, and Puppet use system groups to manage infrastructure provisioning. For instance, a Terraform configuration might define a group policy that grants EC2 launch permissions only to users in the “Cloud-Engineers” group.
This approach ensures that infrastructure changes are auditable, repeatable, and compliant with organizational policies. The HashiCorp website provides extensive resources on how to integrate system groups into IaC workflows.
“System groups are the silent enforcers of order in chaotic development environments.” — DevOps Lead, Sarah Kim
Best Practices for Managing System Groups
Effective system group management is not just about creating groups—it’s about maintaining them with discipline and foresight. Poorly managed groups can lead to security vulnerabilities, access sprawl, and compliance failures.
Principle of Least Privilege
Always assign the minimum level of access necessary for a user to perform their job. Avoid giving administrative privileges to system groups unless absolutely required.
Regularly review group memberships and remove inactive users. Automated tools like AWS IAM Access Analyzer or Microsoft’s Identity Governance can help identify overprivileged accounts.
Regular Audits and Compliance Checks
Conduct periodic audits of system group memberships and permissions. This is especially important for compliance with standards like ISO 27001, SOC 2, or PCI-DSS.
Use logging and monitoring tools to track changes to group memberships. Any unauthorized addition to a privileged group should trigger an alert.
Automation and Lifecycle Management
Integrate system group management into your HR and onboarding systems. When a new employee is hired, automatically add them to the appropriate groups based on their role.
Similarly, when an employee leaves, automate their removal from all system groups. This reduces the risk of orphaned accounts and unauthorized access.
Future Trends in System Group Management
As technology evolves, so too does the concept of the system group. Emerging trends are reshaping how organizations manage access, identity, and system integration.
Zero Trust Architecture and System Groups
The Zero Trust security model assumes that no user or device should be trusted by default, even within the network. System groups play a key role in this model by enforcing strict access controls based on identity, device health, and context.
For example, a user in the “Finance” system group may only access financial systems from company-managed devices and during business hours. This dynamic policy enforcement is made possible through integration with identity providers and endpoint detection tools.
The CISA Zero Trust Maturity Model emphasizes the importance of identity-centric controls, where system groups are central to policy enforcement.
AI-Driven Group Management
Artificial intelligence is beginning to play a role in system group management. AI-powered tools can analyze user behavior and recommend group memberships based on job function, collaboration patterns, and access history.
For instance, if a developer frequently accesses database logs, an AI system might suggest adding them to the “Database-Monitoring” group. These recommendations can be reviewed and approved by administrators, reducing manual workload.
Companies like Okta and Microsoft are already integrating AI into their identity platforms to enhance security and efficiency.
Decentralized Identity and Blockchain-Based Groups
Looking further ahead, decentralized identity systems using blockchain technology could revolutionize system group management. Instead of relying on centralized directories, users could belong to verifiable digital groups that exist on a distributed ledger.
This would enable cross-organizational collaboration without the need for complex federation agreements. For example, a contractor could be temporarily added to a project’s system group with time-bound, cryptographically signed permissions.
While still in early stages, projects like Microsoft’s ION and the Decentralized Identity Foundation are paving the way for this future (Decentralized Identity Foundation).
What is a system group in Linux?
A system group in Linux is a collection of users grouped under a single identifier to manage permissions and access to files, directories, and system commands. Common examples include the ‘sudo’ group, which grants administrative privileges, and the ‘www-data’ group, used by web servers.
How do system groups improve security?
System groups improve security by enabling role-based access control (RBAC), ensuring users only have the permissions necessary for their roles. This minimizes the risk of unauthorized access and simplifies auditing and compliance.
Can system groups be used in cloud environments?
Yes, cloud platforms like AWS, Azure, and Google Cloud use system groups (via IAM) to manage user access to resources. These groups allow administrators to assign roles and policies at scale, ensuring secure and efficient cloud operations.
What are best practices for managing system groups?
Best practices include applying the principle of least privilege, conducting regular audits, automating group membership based on HR data, and integrating system groups with identity governance tools to prevent access sprawl.
How will AI impact system group management?
AI can analyze user behavior and recommend group memberships, detect anomalies in access patterns, and automate provisioning and deprovisioning. This enhances security, reduces administrative burden, and improves compliance.
In conclusion, the system group is far more than a technical detail—it’s a foundational element of modern IT infrastructure, security, and organizational efficiency. From Linux user permissions to cloud IAM policies, system groups enable structured access, streamline operations, and enhance security. As technology evolves with Zero Trust, AI, and decentralized identity, the role of system groups will only grow in importance. By adopting best practices and staying ahead of trends, organizations can leverage system groups to build resilient, scalable, and secure digital environments.
Further Reading: